Distributed Denial Of Service(DDOS) Attack Mitigation
In the current age of big data and internet businesses it is a constant struggle for an organization to prevent data breaches and protect the data of their users. The current landscape of cyber security is still evolving and attempts are being made to use Artifical Intelligence to protect systems from attacks and data breaches.
User data is much valued in the shadowy underworld of darknet. There are amorphous hacker guilds that constantly attack internet sites to compromise the security and data. The attacks come in different forms: SQL injection, social engineering and denial of service attacks.
DDOS Attack
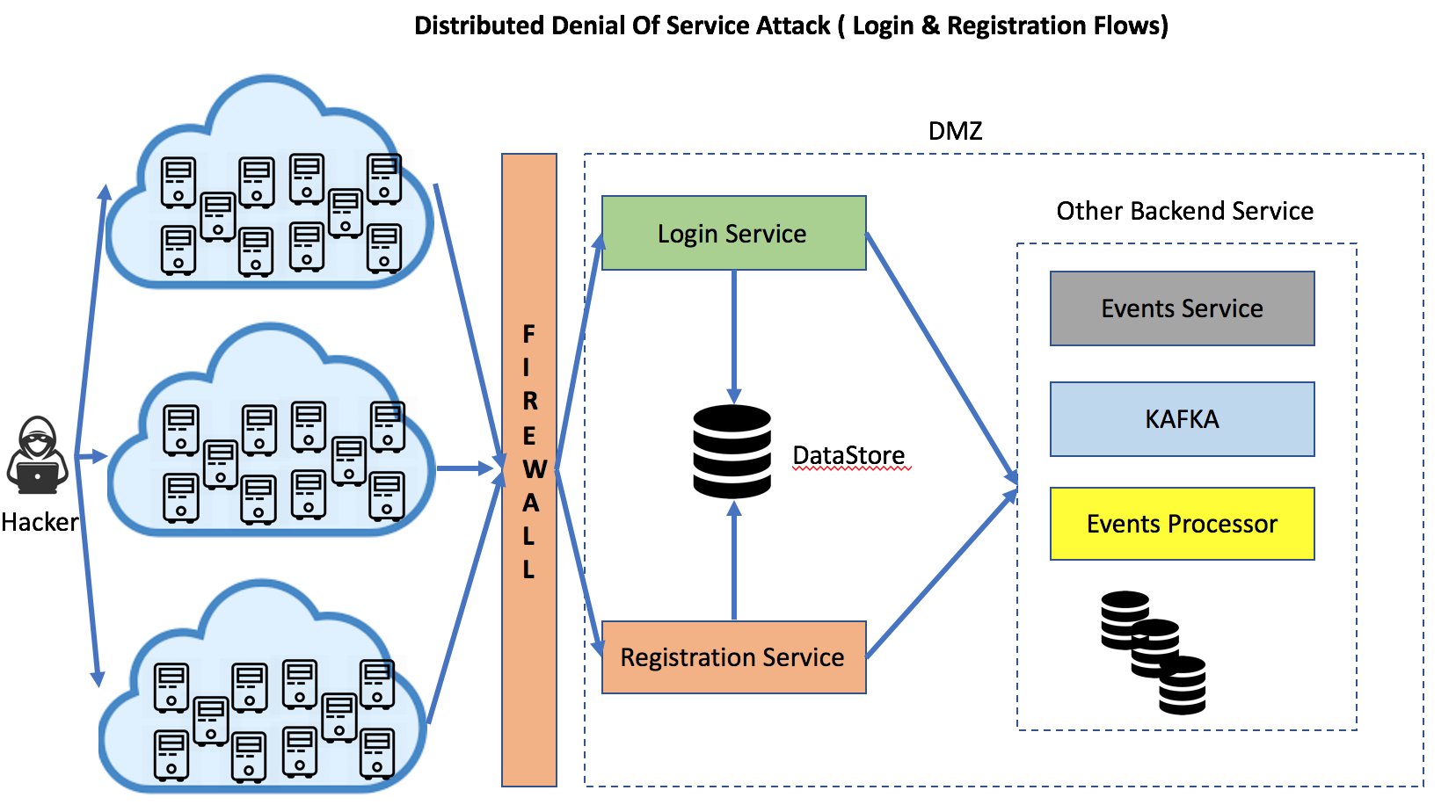
One of the most common and extensive form of attack is the DDOS(distributed denial of service attack). This attack is a brute force attack against a site to obtain credentials for a user on the system. The attacker would use the compromised account to launch social engineering attacks on other users or he can sell the details on the darknet.
Characteristics of DDOS attack
- These attacks are large scale and are known to leverage cloud capabilities to scale requests and widen the attack area.
- DDOS attacks simulates user request and spoof the origin IP address and other request information like the headers. It may not be easy to isolate requests that are part of a DDOS attack to a certain IP address(or range) or to a country/region.
- They cause the application/site to use more than normal computing resource due to increased load. The side effect of this could lead to resource starvation for requests associated with actual user and lead to deteriorated performance of the site or potentially make the system inaccessible to legitimate users.
- Login and registration modules of a site are the first targets for the attackers seeking to gain unauthorized access to the system.
DDOS Mitigation
Its not always possible to completely block DDOS attacks but the impact of it sure can be reduced and its effect mitigated.
Strategies
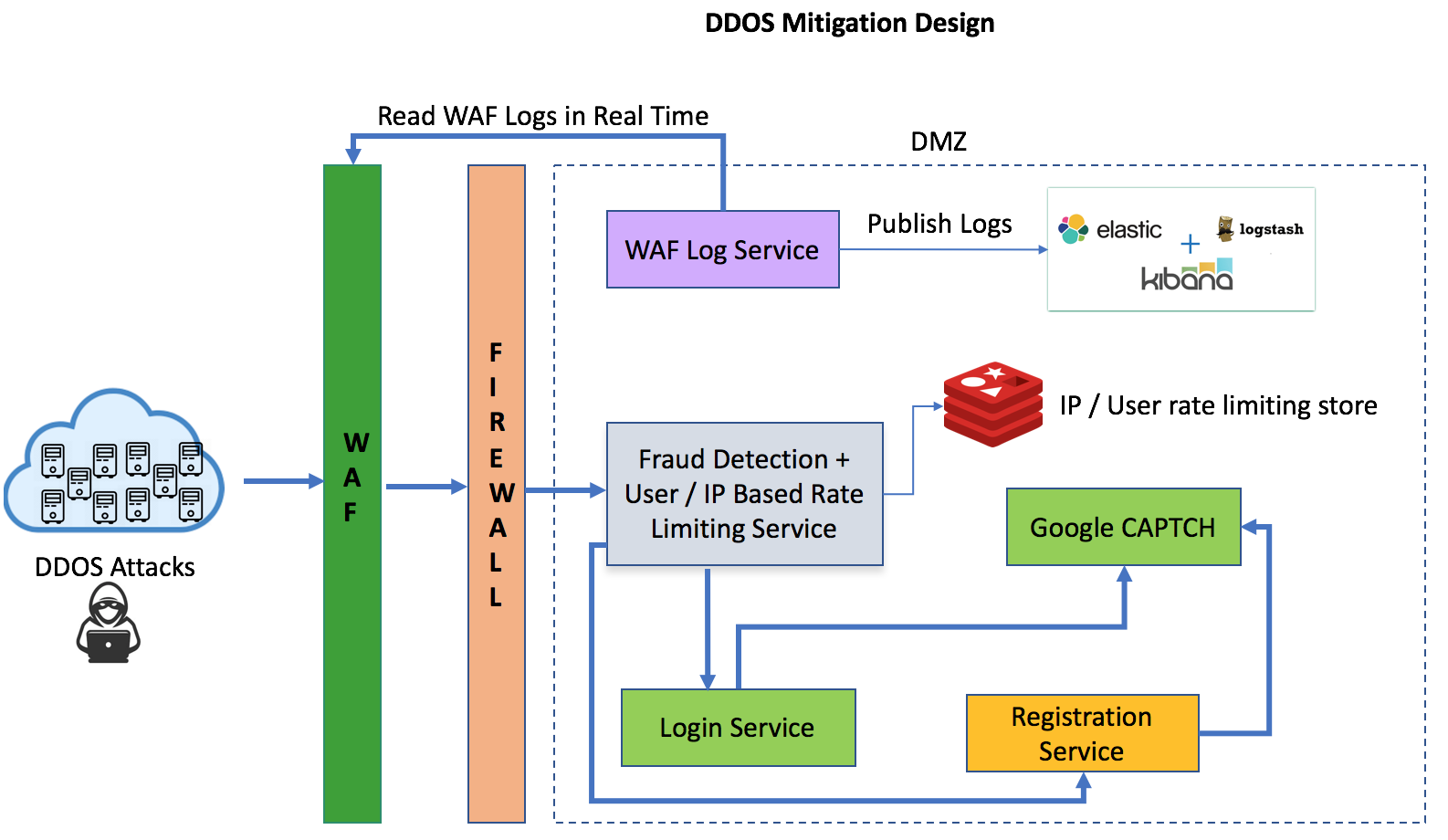
1. Leverage 3rd party WAF (Web Application Firewall) tools. These tools are specifically built to monitor, alert and block certain attack patterns. They act as a reverse proxy to your application/site with added security on top of it. Some well-known WAF are from Cloudflare, Akamai , Incapsula and F5. In addition to DDOS attacks they also help block other attack type like XSS, cookie poisoning, buffer overflow, backdoor entry, stealth commanding etc.
2. Make sure that your services can scale well enough to take the blunt force of the DDOS attack till they can be blocked. Using a public cloud provider will allow you to scale up and down as needed.
3. A true DDOS attack will be difficult for a WAF to block. Mitigating such attack needs more intelligence and data. One can start by monitoring and pulling WAF request logs into their logging/analysis tools like Kibana/Logstash to figure out the URI that is being attacked, the IP address & country from which the requests are originating and the user agent of the request. Looking at these data may help come up with a certain IP address range or country or user-agent patterns which can be added to the WAF rules to block those requests.
4. It is also advisable to add a rate-limiting service in front of your key user facing services(like login/registration modules) to rate limit API requests based on IP address or user agents.
5. Usage of CAPTCHA is also effective in some extent in discouraging the scripts behind the DDOS attack from successfully submitting forms on the site.